Stealing Windows Credentials

Corporate Windows environments have a difficult challenge when it comes to protecting sensitive information stored in memory. It is almost frightening just how much of your personal information and login credentials are sitting in memory in plaintext, sometimes readable by users without administrative privileges!
One such tool, 1responder.py1, is a simple script that can turn your machine into a rogue authentication server for a myriad of protocols. It works for HTTP(S), MYSQL, SMB, DNS, DHCP, among others. Whenever a targeted machine communicates with your rogue server, attempting to authenticate to it, the credentials it uses are harvested and saved. This makes it very easy to get a list of valid hashes on a Windows domain, and because Windows uses hashes for a large number of operations, cracking them is sometimes not necessary.
A new tool was just recently released as well, called Mimikittenz. If you are familiar with the Mimikatz tool (scraping Windows credentials from RAM in plaintext), you will not have to learn much more for this one. Mimikittenz is essentially a rewrite of Mimikatz into PowerShell, creating an open-source scripted version of the tool that you can customize as desired. Additionally, seeing as it uses built-in PowerShell commands, it provides a mechanism for non-administrator users to extract credentials from RAM as well, making it even more versatile than its parent.
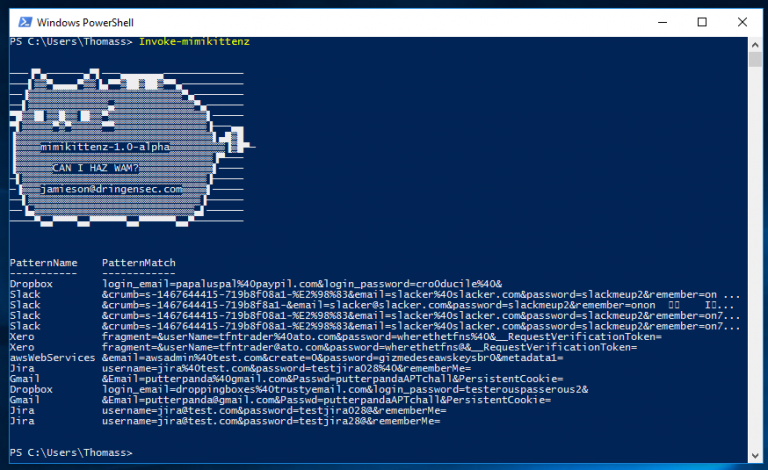
This is definitely not the first time seeing PowerShell used for malicious purposes. Since these are just scripts and not compiled programs, they are trivial to get past any antivirus system and other safeguards. If PowerShell is not disabled for your users, be on the look out for malicious scripts like these.
For more information on Responder: https://github.com/SpiderLabs/Responder For more information on Mimikittenz: https://github.com/putterpanda/mimikittenz
