n00bs CTF Level 13
| Link: Webpage | Points: 130 |
Useful Tools: file wireshark |
Tags: beginner web network |
Show Solution …
The Challenge
The main page of level 13 has nothing but a block of text telling us that we are apparently on the wrong page. Nothing is clickable, there are no pictures or other files to be seen, and the source code does not reveal anything notable.
It is hinting to us that there may be a backup of the correct webpage on here. Looking at the URL, we are on /levelthirteen.php as expected, so perhaps there is another page for the backup?
Let’s just give some common names a try… some of the methods I tried was directing the browser to some guessed folders of the website, such as /archive, /backup, /backups, etc. No luck; none of these existed. Then I tried looking for similarly named files within the same folder instead, such as /levelthirteen.php.backup and /levelthirteen.php.old. The later guess was valid, and I was able to download the backup for analysis.
Opening this file in a text editor to see the source code. Since we are viewing the contents of a PHP file, we are able to see the PHP code as well, which isn’t visible when viewing the source in a browser.
< clipped >
<div class="hero-unit lvlfour">
<h1>
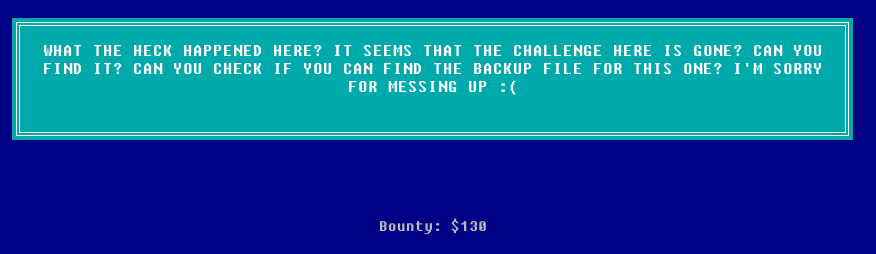
What the heck happened here? It seems that the challenge here is gone?
Can you find it? Can you check if you can find the backup file for this one?
I'm sorry for messing up :(
</h1>
<?php
/* <img src="img/clippy1.jpg" class="imahe" /> <br /> <br />
<p>Do you want to download this mysterious file?</p>
<a href="misc/imadecoy">
<button class="btn">Yes</button>
</a>
<a href="index.php">
<button class="btn">No</button>
</a>
*/
?>
</div>
< clipped >It refences a file called “imadecoy” but I downloaded it for analysis anyways. Not knowing what the file type was, I ran it through file:
$ file imadecoy
imadecoy: tcpdump capture file (little-endian) - version 2.4 (Linux "cooked", capture length 65535)Looks like it’s a packet capture. Let’s open it up in Wireshark. We see a lot of HTTP (unencrypted) traffic, so I try examining a list of the HTTP objects that were downloaded in these packets. You can do this in Wireshark by clicking File –> Export Objects –> HTTP. Doing so will give you a listing.
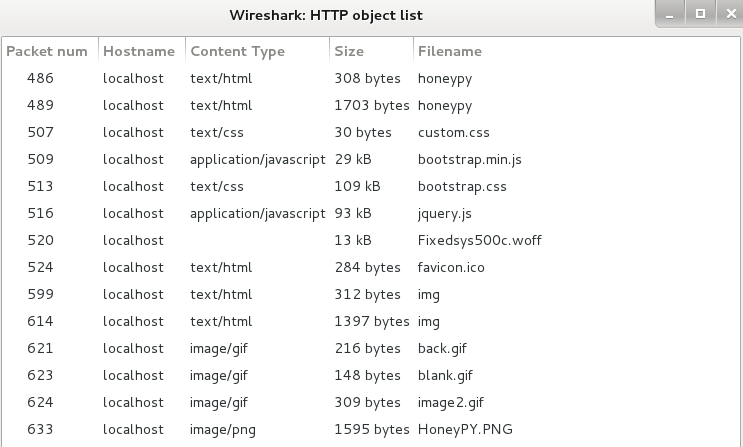
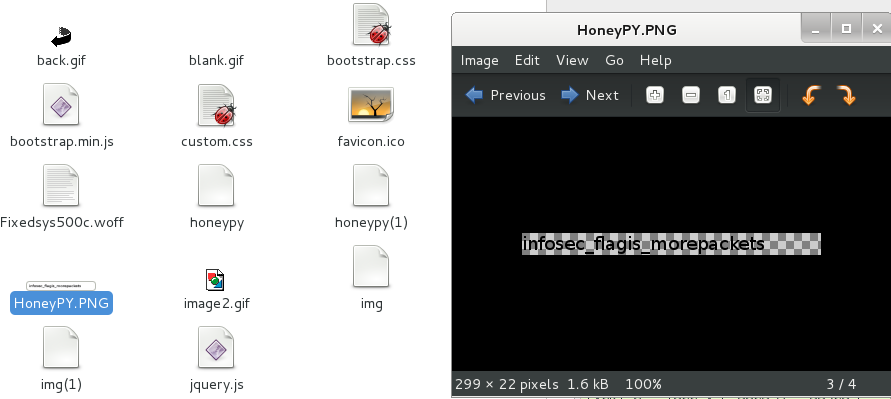
You can’t really tell if there is anything valuable in here just by looking at the names, so let’s start digging through all of them. I export them all to a folder and immediately notice that one appears to be a single line of text like our flag. I opened it up to be sure, and as luck would have it, found the flag infosec_flagis_morepackets
Lessons Learned
A very common convention to backup files in Linux is just to add .old to the end of the file. This isn’t a requirement, but knowing the common convention is really the only way correctly guess the name of the backup file. Checking for backup files can be valuable; maybe the old file had some credentials hard-coded in it that they removed in the current version, or perhaps you can use it to view PHP source code that is otherwise invisible to you.
We also used the file command again, this time really proving its worth because it would have been very difficult to determine the filetype for imadecoy without it.
We learned some new Wireshark skills as well: exporting HTTP objects that were downloaded throughout the duration of the packet capture.
