n00bs CTF Level 5
| Link: Webpage | Points: 50 |
Useful Tools: steghide |
Tags: beginner stego |
Show Solution …
The Challenge
Before we’re presented with the main page of this level, we have what seems to be an endless stream of popups preventing us from getting through that all say “Hacker!!!” (looks like they’re on to us). Luckily, most browsers won’t accept that for long, and your pop-up should provide you with an option that says something similar to “Prevent this page from creating additional dialog boxes” after two or three of these come up.
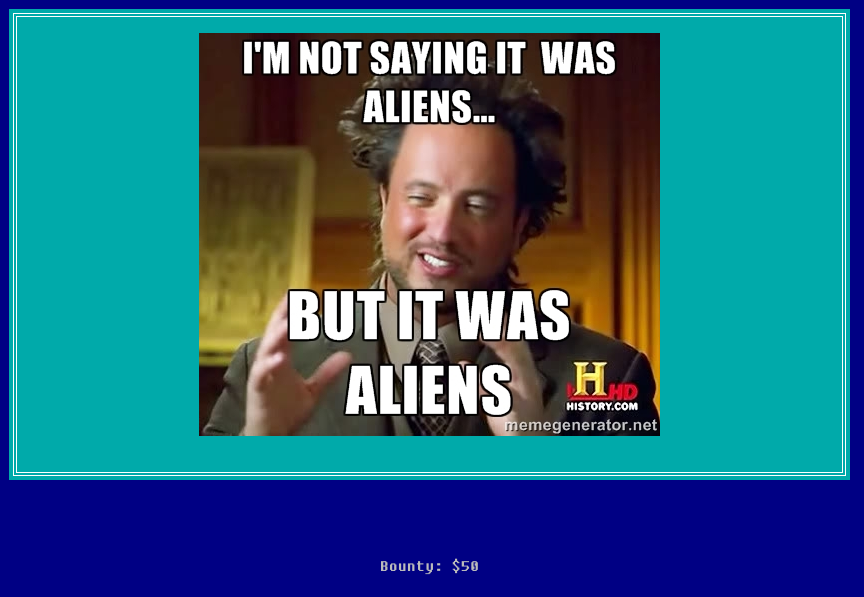
We now reach the main page. It is fairly minimal, consisting of just an image. As with any challenge, take a look through the source for more clues on where to look next. In this case, there isn’t much there either, and there aren’t any new cookies.
There isn’t much left to examine besides the picture, so let’s download it and see if it has anything hidden away inside. You can use a tool like exiftool on Linux to take a deep look into the metadata for clues, but in this case there is nothing there. Running out of options, we can try looking for any steganography, or hidden data within the image itself. I did this with Linux, but you could also download a Windows steganography program (like SilentEye) instead. To do it with Linux, I used the steghide tool. If the image doesn’t have any steganography in it, it will come up blank, so no harm in trying. It will ask you for a password, but seeing as I had no idea what that would be, I just left it blank.
$ file aliens.jpg
aliens.jpg: JPEG image data, JFIF standard 1.01, resolution (DPI), density 72x72, segment length 16, baseline, precision 8, 461x403, frames 3
$ steghide extract -sf aliens.jpg
Enter passphrase:
wrote extracted data to "all.txt".
$ cat all.txt
01101001011011100110011001101111011100110110010101100011010111110110011001101100011000010110011101101001011100110101111101110011011101000110010101100111011000010110110001101001011001010110111001110011I sent that string over to a binary-to-ASCII converter, and it decodes into the flag: infosec_flagis_stegaliens
Lessons Learned
This level may have left you banging your head for a while. There was a lot that you probably tried before jumping right into steganography, but all would have come up short for anything useful. In all of these levels, the most important lesson is maintaining persistence to complete the challenge. Don’t give up! The answer won’t always be obvious.
This may have also been your first experience with steganography. You learned how to pull embedded data out of a seemingly innocent image file, and conversely, you could learn how to put data in there yourself with just another few minutes of experimenting.
Lastly, you gained a third decoder to put in your back-pocket for future use!
