n00bs CTF Level 9
| Link: Webpage | Points: 90 |
Useful Tools: Google |
Tags: beginner web |
Show Solution …
The Challenge
We are given a login prompt for what appears to be the web interface of a Cisco Intrusion Detection System (IDS). A quick look at the source code does not provide very much additional information.
You should try any combination of username and password that you think might get you in. Typical default usernames/passwords are admin/admin, admin/password, root/root, etc. After a while, you may end up needing some help because your attempts all fail. Before brute forcing further, let’s see if there is a documented default username/password that ships with a standard Cisco IDS web interface.
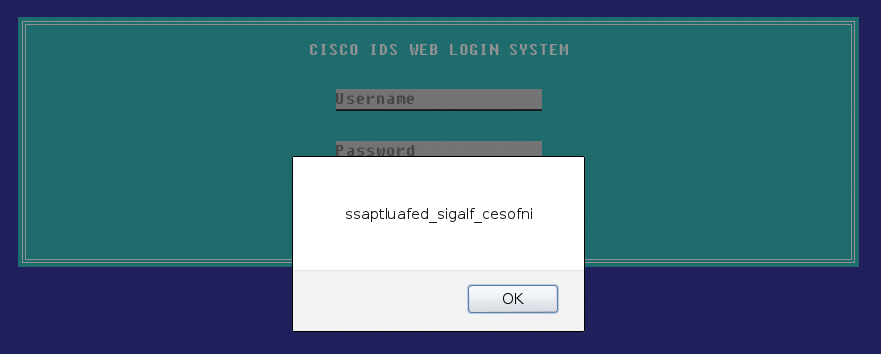
We don’t even have to click the link, just read the description. I gave root/attack a try, and sure enough, it was successful! The result was a dialog box like the one below.
Look familiar? At first glance, this looks similar to what we saw a few levels ago where the flag was encrypted through a substitution/rotation cipher. We can still see the underscores and it appears similar to the flag, however the underscores are not in the proper place. It’s also not a straight-forward substitution either seeing as it starts with ss yet the beginning of the actual flag is two different letters in. Maybe it’s a more advanced form of crypto than a simple substitution cipher?
As I started to write it down to attempt some other decryption methods, I realized that the answer was right in front of my eyes the whole time. The flag is just written backwards; reading it forward gives infosec_flagis_defaultpass
Lessons Learned
When you see a login prompt, always search for default credentials for the application that you are logging in to. Many times you will find that they still work. Plenty of websites exist that store the default credentials for a wide variety of applications.
Conversely, make sure to change the default password when you install new services. These passwords are widely known and published.
Finally, a repeat lesson-learned here is pattern recognition. It took me longer than I would have liked to notice that the flag was simply reversed. Not noticing simple patterns can cost significant time due to trying more complicated analysis than is needed, so catching these right away is highly valuable.
