n00bs CTF Level 14
| Link: Webpage | Points: 140 |
Useful Tools: file cat |
Tags: beginner web |
Show Solution …
The Challenge
Looks like we’re back to downloading files for offline analysis again. Check on the source code to make sure you don’t waste any time, and then go ahead and download the file.
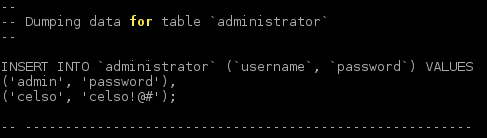
The file will open in your browser, but I chose to copy it into a file so that I could open it offline. As explained at the top of the file, this is a phpMyAdmin SQL dump, or a dump of everything in all of the databases for some webpage running phpMyAdmin. One of the first things that caught my eye was some administrator usernames and passwords.
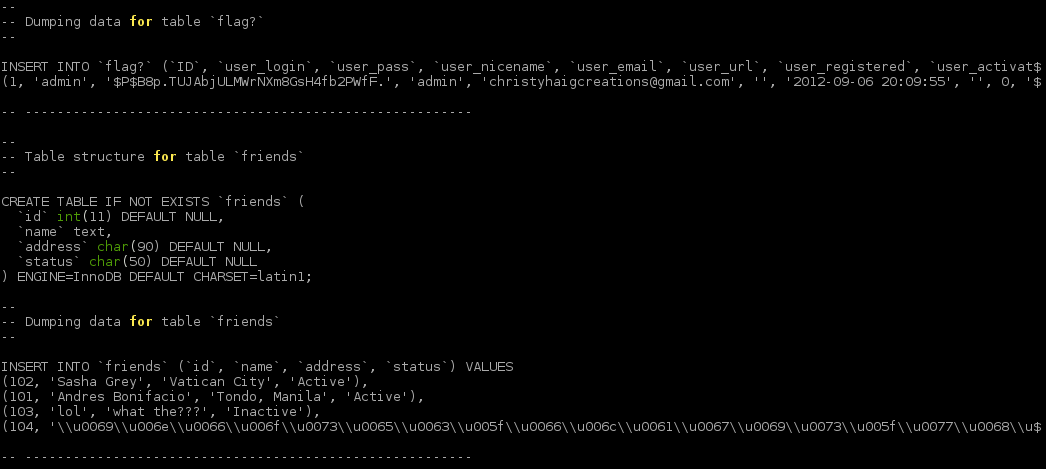
Moving on past that, there was a flag? table that, of course, warranted some exploring. The image below contains the dump of the flag table as well as the friends table.
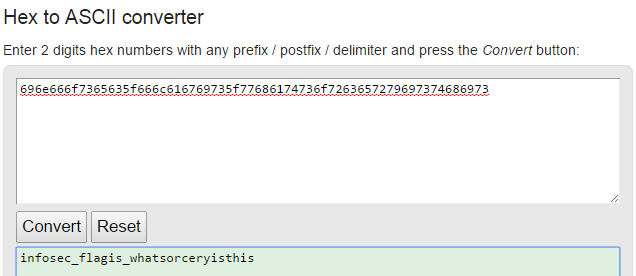
Because the flag table was more enticing, I tried cracking the admin password hash with john, but I wasn’t able to get anywhere very fast. While the dictionary attack was running, I noticed the very odd line on the bottom of the friends table. It looks like a bunch of hex values, although separated by \\u00 every time, and notice that many are in the 60s-70s, which is again a good indicator that these are hex-encoded ASCII characters. Let’s strip off the \\u00 parts and decode the remaining hex. This gives us our flag infosec_flagis_whatsorceryisthis
Lessons Learned
This was a lot of text to sift through, and unfortunately just doing a search for the flag comes up empty. This again comes down to recognizing when something seems odd or interesting; knowing what is normal versus not normal. The usernames, passwords, and hashes were interesting, but we weren’t provided a login prompt to use them. The line at the end of the friends table was definitely odd-looking, and deeper inspection showed a pattern of hex values in the 60s-70s which should raise some red flags, as this was the third or fourth time now that we’ve seen a pattern of ASCII characters encoded as hex.
