n00bs CTF Level 7
| Link: Webpage | Points: 70 |
Useful Tools: base64 Live HTTP Headers |
Tags: beginner web |
Show Solution …
The Challenge
When you go to level seven via the Levels() dropdown box (as you normally do), you will be brought to the page shown below. You can look at the source code all you like, even look at your cookies and headers, but you won’t find anything here this time.
f00 not found
Something is not right here???
btw...bounty $70This one calls out your attention to detail, like many CTF challenges do. You may or may not have noticed that each level has been named /levelone.php, /leveltwo.php, and so on. So we should be on /levelseven.php now then, right? Take a look at your URL; the dropdown box to take you to level 7 brought you to /404.php. Strange.
Seeing as there isn’t anything here, let’s try going directly to /levelseven.php ourselves by manually typing it in the address bar of the browser. Doing so take us to a completely blank, white page with nothing on it at all. Even the source code is completely empty. This tells us something is here, though; if the page didn’t exist, we would have gotten an error from the server. The fact that we have this blank page means this page does actually exist and must do something that it’s not telling us. One thing that we haven’t tried in previous challenges is looking at the header content of HTTP requests.
This header content I’m referring to is different from the <head> ... </head> section of HTML source code. Instead, I’m referring to the actual HTTP headers, the information that is included with GET/POST requests and server responses. There are a variety of ways to view this information, such as capturing your traffic with Wireshark, using an intercepting proxy, or using the developer tools (F12) of your browser. We already used an addon for Firefox to view and edit cookies earlier, so I’ll introduce another Firefox addon to view header data.
Live HTTP Headers is a great addon to view your header traffic. Once installed, you can launch it in the Tools menu of Firefox to start capturing. Refresh the blank challenge page, and you’ll see the header traffic appear.
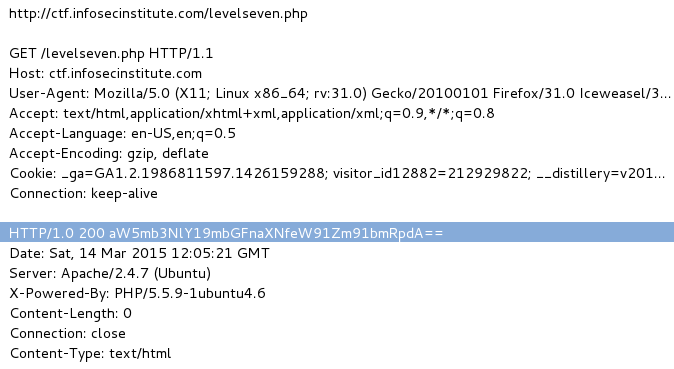
As always, being able to identify patterns or other interesting lines of text can save you a lot of time. The line highlighted above should jump out to you as being “potentially interesting” like that. From our previous lessons learned, you should also be able to identify what this text is. You see lowercase and uppercase characters, numbers, and some “=” signs at the very end, which tells you that this is more than most likely a base64-encoded string.
Send it through the decoder that you used on level two and you’ll get the flag: infosec_flagis_youfoundit
Lessons Learned
This is yet another case of “don’t trust anything in a CTF challenge.” Your trusty level-selector drop-down box brought you to the wrong place, and you had to figure out the right location based on noticing a standard naming convention.
Throughout a CTF challenge, attention to detail is absolutely critical. Make mental or physical notes when you notice naming conventions or other patterns; it may be useful later.
We also learned about examining HTTP headers. It’s another good place to look if you don’t find any clues in the source code or cookies.
Finally, we revisited a past lesson on the identification and decoding of base64 strings. Knowing what doesn’t look normal will take some experience, but you will find that you pretty much always want to try decoding any base64 strings you see; there is usually always some kind of valuable data behind it, at least in a CTF.
