| Link: Webpage | Points: 110 |
Useful Tools: file exiftool strings base64 |
Tags: beginner stego |
Show Solution …
The Challenge
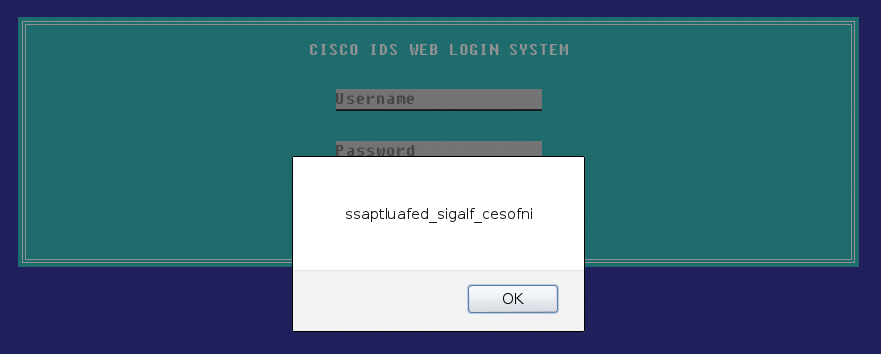
Level 11 provides us with a fairly odd-looking page from the start.
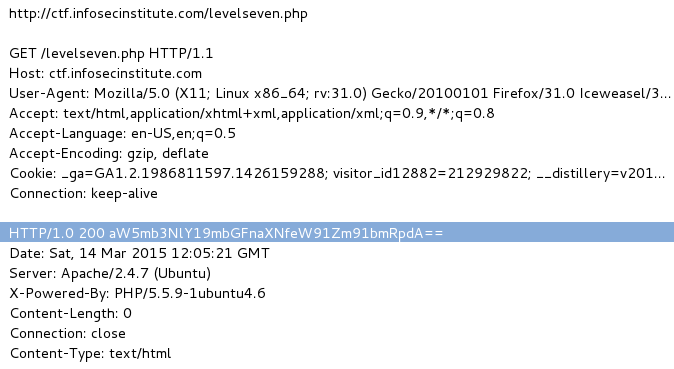
Looking for more details, the php image file has an interesting name. You can see its name either by looking at the source code, viewing its direct path, or opening its properties in the browser. I happened to look at its properties:
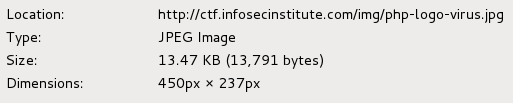
I downloaded the file to analyze it further. Seeing as it calls itself a virus, I ran it through the Linux file command to verify whether or not it was a picture, but sure enough it said that it was indeed a valid jpeg image.
$ file php-logo-virus.jpg
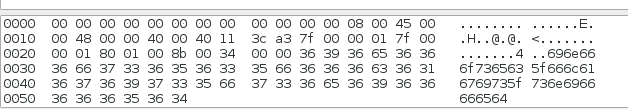
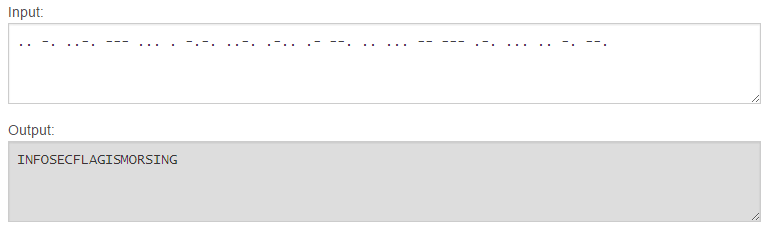
php-logo-virus.jpg: JPEG image data, JFIF standard 1.01, resolution (DPI), density 96x96, segment length 16, Exif Standard: [TIFF image data, big-endian, direntries=6, name=infosec_flagis_aHR0cDovL3d3dy5yb2xsZXJza2kuY28udWsvaW1hZ2VzYi9w], baseline, precision 8, 450x237, frames 3We actually get the flag right there in the file information! If you didn’t think to run file on the image, you can also find the flag in the image’s metadata (which is where file found it as well, but that won’t always happen).
$ exiftool php-logo-virus.jpg
ExifTool Version Number : 10.10
File Name : php-logo-virus.jpg
< clipped >
X Resolution : 96
Y Resolution : 96
Exif Byte Order : Big-endian (Motorola, MM)
Document Name : infosec_flagis_aHR0cDovL3d3dy5yb2xsZXJza2kuY28udWsvaW1hZ2VzYi9wb3dlcnNsaWRlX2xvZ29fbGFyZ2UuZ2lm.
Profile CMM Type : Lino
Profile Version : 2.1.0
< clipped >You could have also found it with strings
$ strings php-logo-virus.jpg
JFIF
Exif
infosec_flagis_aHR0cDovL3d3dy5yb2xsZXJza2kuY28udWsvaW1hZ2VzYi9wb3dlcnNsaWRlX2xvZ29fbGFyZ2UuZ2lm
Photoshop ICC profile
XICC_PROFILE
HLino
mntrRGB XYZ
< clipped >However you get there, we’re still not done yet. This doesn’t follow the standard flag format; we need to decode the long string at the end of the flag. Since it has a combination of lowercase, uppercase, and numbers, let’s try base64.
$ echo aHR0cDovL3d3dy5yb2xsZXJza2kuY28udWsvaW1hZ2VzYi9wb3dlcnNsaWRlX2xvZ29fbGFyZ2UuZ2lm | base64 -d
http://www.rollerski.co.uk/imagesb/powerslide_logo_large.gifVisiting this link gives us an image with text, and that text is the final part of the flag infosec_flagis_powerslide
Lessons Learned
This was another case of attention to detail. The name of the file was a clue to focus on that file. There were many ways of identifying this flag, so understanding each and why they work is beneficial. Remember that you can use grep to search for the flag, as well.
Also, we were once again given a base64 encoded string. This is the third time decoding base64 in this CTF, so hopefully you’re starting to be able to identify it more quickly now and immediately decoding it.